- 29 Mar 2023
- 3 Minutes to read
- Print
- DarkLight
Single Sign On
- Updated on 29 Mar 2023
- 3 Minutes to read
- Print
- DarkLight
Single sign-on is an authentication system that allows a user to log in with a single ID and password to any of related, yet independent software systems.
SSO services allow users to use a set of login credentials (e.g., email and password) to access multiple applications. The service authenticates the end-user's credentials only once for all the applications according to the rights given to the user.
Overview
A very common example is Google’s SSO implementation of login for their products, such as Gmail, YouTube, and so on. Any user logged in to one of Google’s products is automatically logged in to their other products as well.
Some common advantages of SSO:
- Removes the need for users to remember and manage multiple passwords.
- Simplifies user’s experience by allowing them to log in at one single access point and enjoy a seamless experience across multiple applications.
- Increases productivity significantly by reducing password-related support emails.
- Reduces phishing and thereby makes sure that users aren’t tricked into giving away sensitive information.
Prerequisite
- Should be a registered user on the pCloudy platform
- The Profile of the user should be validated
- An Azure subscription (as we have taken Azure as an example here). Or as per user need, it can be okta, Azure
Steps
A) Configuration needed from Infra /IT
Note: We have taken Azure AD SSO as an example
Follow these steps to enable Azure AD SSO in the Azure portal.
- In the Azure portal, Create the app and select single sign-on (manage section).
- On the Select a single sign-on method page, select SAML.
- On the Set up single sign-on with SAML page, click the edit/pen icon for Basic SAML Configuration to edit the settings.
- Please ensure that the default checkbox as shown in below screenshot is checked
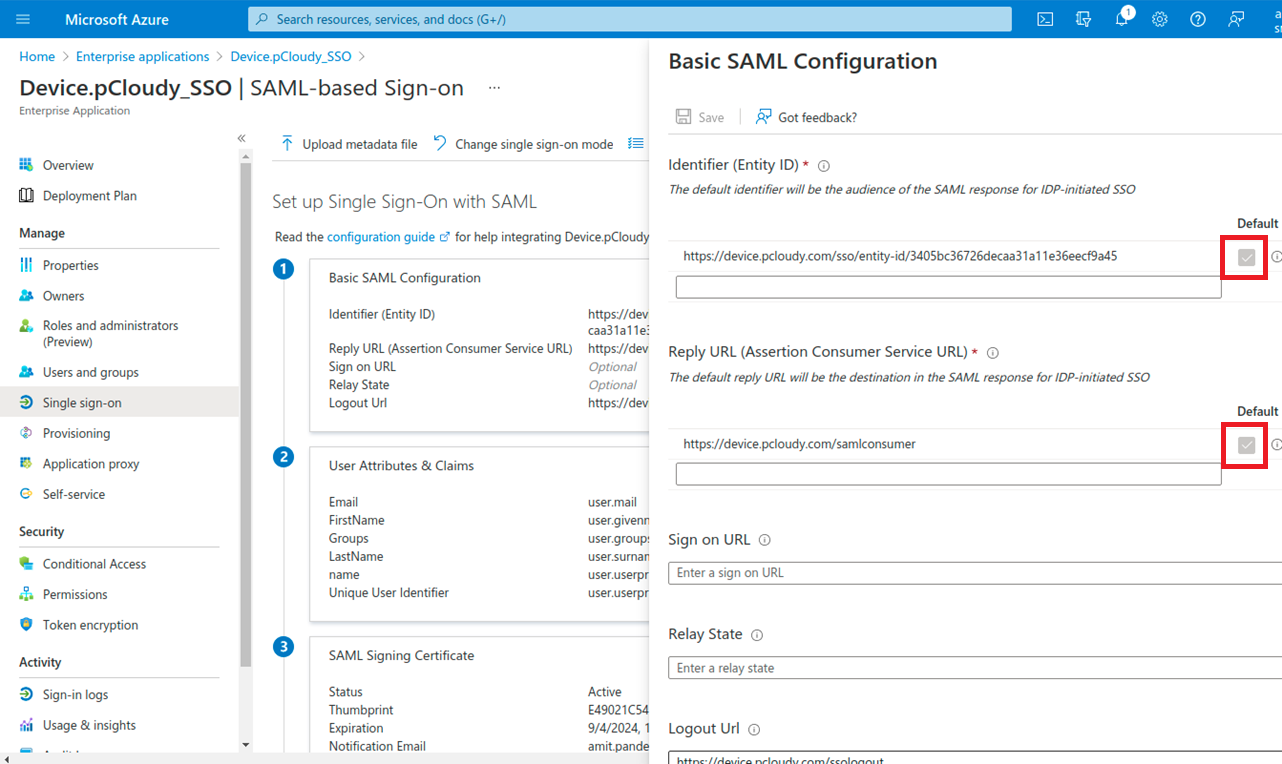
For Reply URL: Paste the reply URL in SAML configuration
E.g. https://device.pcloudy.com/samlconsumer

For Logout URL: Paste log out URL in SAML configuration
E.g. https://device.pcloudy.com/ssologout

Custom attributes need to be created in a special format. As shown in the below screenshot.
- FirstName
- Groups
- LastName

In the SAML Signing Certificate section, find Federation Metadata XML and click on Download. Open metadata.xml in some editor and copy Certificate which is required to fill the SSO form.
In the metadata.xml file Certificate section will look like in the format shown below

Note: The user needs to paste this section only in the SSO form (certificate field value).

Copy the Azure AD Identifier. This will be needed to add in the 'IdP issuer’ field in SSO form.

Go to the SAML Properties page and copy the User access URL. This will be needed to add in the 'IdP Single Sign On URL’ field in SSO form.

These are the configurations needed from Infra/IT. Once this is done, the user will need to convert a normal account to SSO.
B) Steps to migrate the user account to SSO
- User needs to login into the pCloudy platform. On the Start page, Click on Integration on the Left Panel.
- Fill all required fields -Identity Provider, IdP Issuer, Display Name, Domain name, IdP Single Sign-On URL, and Certificate to Validate Signature. Click on “Save”
- IdP Identity Provider: An identity provider is “a trusted provider that lets you use single sign-on (SSO) to access another website. E.g. Azure
- IdP Issuer/ IdP Entity ID: This field corresponds to the “Idp Entity ID” field available in the SSO Configuration window. Here, you will need to paste the copied Azure AD Identifier.
- Display Name: E.g. pCloudy
- Domain Name: E.g. sstsinc.com
- IdP Single Sign-On URL: This field corresponds to the “IdP Single Sign-On URL” field available in the SSO Configuration window. Here, you will need to paste the copied User access URL from the SAML Properties page
- Certificate to Validate Signature: this field corresponds to the "IdP certificate" available in the SSO Configuration window. Copy and paste the certificate accordingly.
- Once you have filled in all the details Click Save. A unique "Entity ID" will be generated, which you can copy and use to update in the SSO Configuration.
- User needs to inform their IT/Infra team to update the generated Entity ID in SSO configuration form Under SP Entity ID field. Refer to the below screenshot.

Once the whole process is complete, users can use one set of login credentials and access multiple applications.
Note: Application permission needs to be provided from the infra/IT team
End-user credentials get authenticated only once for all the applications according to the rights given to the user.


